Understanding Reverse Proxy – Features, How It Works, and Applications
- Published on
- What is Reverse Proxy?
- Practical Applications of Reverse Proxy
- System Security
- Load Balancing
- Caching
- SSL Termination
- Issues That May Arise When Using Reverse Proxy
- Increased System Complexity
- Issues with SSL Termination
- Scalability Limits
- Compatibility Issues with Applications
- Comparing Reverse Proxy and Forward Proxy
- Function and Use Case
- Deployment Location
- Operation
- Security Usage
- Applications
- Overview Comparison Table
- Basic Guide to Using Reverse Proxy
- Configuring Reverse Proxy with Nginx
- Configuring Reverse Proxy with Apache
- Notes When Using Reverse Proxy
- Conclusion
What is Reverse Proxy?
Reverse Proxy is a service or intermediary server that acts as a protective layer between users and the actual servers in a network system. When users send requests to a website or an online service, the request is not directly sent to the origin server but is instead routed through the reverse proxy. The reverse proxy then decides how to handle the request, which can include forwarding it to other backend servers or returning data from the cache.
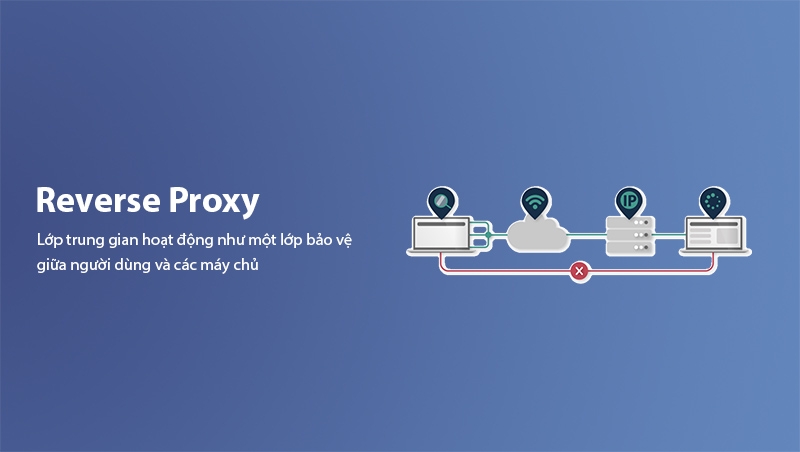
This helps hide the IP addresses of the backend servers, protecting the system from direct attacks from the outside. Reverse Proxy acts as a security layer, filtering requests before they reach the actual servers, thereby protecting backend servers from threats such as DDoS (Distributed Denial of Service) attacks.
In addition, reverse proxy can help improve system performance through features like load balancing and caching. Load balancing helps distribute requests among backend servers, ensuring the system runs smoothly and avoids overload. Caching reduces access time and data reload by temporarily storing frequently requested content.
With these outstanding features, reverse proxy is not only an important tool for security but also plays a significant role in optimizing the performance of modern web services. You can read more in the article What is a Proxy? to better understand what a proxy is.
Practical Applications of Reverse Proxy
Reverse Proxy is not only a security tool but also has many real-world applications in optimizing performance, protecting systems, and managing traffic for web services. Here are some common applications of reverse proxy:
System Security
One of the most important applications of reverse proxy is security. When backend servers are not directly exposed to users, reverse proxy serves as a protective layer, preventing external attacks. As a result, the origin servers are not exposed and avoid the risk of direct attacks.
Reverse proxy can block attacks like DDoS (Distributed Denial of Service), where fake requests from millions of devices are sent to the server to overwhelm or crash the service. The reverse proxy filters requests and only forwards valid ones to the backend servers, reducing the impact of such attacks.
Load Balancing
Reverse proxy can help with load balancing between backend servers to distribute user requests evenly. This is critical in high-traffic systems, ensuring that backend servers are not overloaded and improving the system's responsiveness.
When a request arrives, the reverse proxy decides to forward it to a backend server that is less busy or has fewer requests. This helps optimize system resources, improve performance, and maintain stable service.
Caching
Another application of reverse proxy is caching. Reverse proxy can store static data or web content (such as images, HTML pages) in its cache. When a user sends a request to access these contents, the reverse proxy returns the data from the cache instead of asking the backend server to process it again. This helps reduce the load on backend servers and improves access speed for users.
Caching also helps reduce bandwidth usage, as the cached data will be reused rather than reloaded from scratch every time a new request comes in. This is especially useful in web services with high traffic and frequently requested content.
SSL Termination
SSL termination is another important feature of reverse proxy. When using SSL (Secure Sockets Layer) to encrypt connections, reverse proxy can handle the SSL decryption, process encrypted requests, and then forward them to backend servers. This helps reduce the load on backend servers, as these servers no longer need to perform resource-intensive encryption and decryption tasks.
Additionally, reverse proxy can help enhance security for SSL connections by ensuring that all connections between users and the proxy are encrypted, protecting transmitted data from stealthy attacks.
With these applications, reverse proxy plays an essential role in optimizing systems, safeguarding data, and improving the performance of web services.
Issues That May Arise When Using Reverse Proxy
Although Reverse Proxy offers many benefits in terms of security, performance, and system management, there are still some issues that may arise when deploying and using it. Here are some common problems that may occur with reverse proxy usage:
Increased System Complexity
Using reverse proxy can increase the complexity of configuring and managing the system. Requests from users must go through an intermediary layer before reaching the backend servers, which can introduce potential points of failure. If an issue occurs at the reverse proxy level, it could impact the entire system, especially if the reverse proxy is not properly configured or monitored.
Issues with SSL Termination
While SSL termination is a benefit of reverse proxy, it can also cause issues if not implemented correctly. One common problem is the transmission of encrypted data from the reverse proxy to the backend servers without securing it via SSL. This can expose sensitive information if the connection between the reverse proxy and backend servers is not properly secured.
Additionally, SSL termination on reverse proxy requires robust hardware and software capable of handling encryption and decryption processes. Without the proper resources, this may reduce system performance.
Scalability Limits
Although reverse proxy helps distribute requests across backend servers, it can also become a bottleneck in the system if not properly configured. When traffic surges suddenly, the reverse proxy may not be able to handle all requests quickly, leading to congestion and reducing the overall system performance.
To address this issue, reverse proxy needs to be configured to be scalable and have mechanisms in place to automatically scale resources as traffic increases.
Compatibility Issues with Applications
Some web applications may encounter compatibility issues when using reverse proxy. This is especially true for applications that rely on specific protocols or features that the reverse proxy cannot support or forward accurately. For example, if the application uses cookies or session states to maintain connections, the reverse proxy must be configured to ensure that this information is not lost when requests are forwarded.
Moreover, applications that require direct processing from the origin server may face difficulties when routed through reverse proxy, leading to disruptions or performance degradation.
While these issues can be resolved through careful configuration and monitoring, using reverse proxy requires attention and a clear understanding of the technical factors and system environment.
Comparing Reverse Proxy and Forward Proxy
To better understand the role and application of Reverse Proxy, we need to compare it with Forward Proxy, another popular type of proxy. Although both are intermediary servers, they operate differently and serve distinct purposes. Here are some key differences between Reverse Proxy and Forward Proxy:
Function and Use Case
-
Reverse Proxy: A proxy located on the server side that handles requests from users. It acts on behalf of backend servers, coordinating requests and returning results to users. Reverse proxy is mainly used for security, load balancing, and system performance improvement. It hides the origin servers and protects them from external threats.
-
Forward Proxy: On the other hand, forward proxy primarily operates on the user side. When users request access to a website, the request is first sent to the forward proxy, which then forwards it to the target server. Forward proxy helps control internet access, anonymize users, and block unwanted websites.
Deployment Location
-
Reverse Proxy is usually deployed at the organization's or web service's servers, responsible for receiving and handling user requests before forwarding them to the actual servers.
-
Forward Proxy is typically deployed on the user side or within the internal network of an organization, where it can regulate and monitor outgoing traffic from the internal network to the Internet.
Operation
-
Reverse Proxy receives requests from users and decides which backend server to forward the request to. After receiving data from the backend server, the reverse proxy returns the result to the user.
-
Forward Proxy receives requests from users and forwards them to the target server the user wants to access. After the target server responds, the forward proxy sends the result back to the user.
Security Usage
-
Reverse Proxy helps protect backend servers from external attacks by hiding the actual servers and only forwarding valid requests. It also supports security features like SSL termination and caching.
-
Forward Proxy helps protect users from online threats by anonymizing their IP addresses and can block harmful or unwanted websites. Forward proxy can also help organizations monitor and control the online activities of employees or students.
Applications
-
Reverse Proxy is used in complex web systems with multiple backend servers to improve performance, security, and load management. Common reverse proxy services include nginx, HAProxy, and Traefik.
-
Forward Proxy is used to control internet access, hide user identities, and filter web content. Common forward proxy services include Squid, Tor, and corporate proxy servers.
Overview Comparison Table
Below is a comparison table between Reverse Proxy and Forward Proxy in HTML format:
| Criteria | Reverse Proxy | Forward Proxy |
|---|---|---|
| Function and Purpose | Used for security, load balancing, and improving system performance by hiding backend servers from users. | Helps control internet access, anonymize users, and block unwanted websites. |
| Deployment Location | Deployed on the server side, between the user and backend servers. | Deployed on the client side or within an organization's internal network. |
| How It Works | Receives requests from users and forwards them to the backend server, then returns the results to the user. | Receives requests from users, forwards the request to the destination server, and sends the results from the destination server back to the user. |
| Security Purpose | Helps protect backend servers from external attacks, supports SSL termination, and caching. | Helps anonymize users and block malicious websites, filters web content. |
| Applications | Used in complex web systems with multiple backend servers, e.g., nginx, HAProxy, Traefik. | Used to control internet access, hide users' identities, e.g., Squid, Tor. |
In summary, although Reverse Proxy and Forward Proxy both serve to improve system performance and security, they operate at different levels and environments, serving different purposes in managing and optimizing internet connections.
Basic Guide to Using Reverse Proxy
Implementing and configuring a Reverse Proxy can help optimize performance and security for your web system. Below is a basic guide to setting up a reverse proxy using popular tools like Nginx and Apache.
Configuring Reverse Proxy with Nginx
Nginx is one of the most popular tools for setting up a reverse proxy due to its fast processing and flexible configuration. Here are the basic steps to configure a reverse proxy with Nginx:
-
Install Nginx: First, you need to install Nginx on your server. On Ubuntu, you can install Nginx with the command:
sudo apt update sudo apt install nginx -
Configure Reverse Proxy: After installing Nginx, you need to edit the Nginx configuration file to set up the reverse proxy. Open the configuration file:
sudo nano /etc/nginx/sites-available/defaultThen, add the following configuration inside the
serverblock:server { listen 80; server_name example.com; location / { proxy_pass http://localhost:8080; # Backend server address proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; } }In this configuration:
proxy_passis the backend server address to which the reverse proxy will forward requests.- The
proxy_set_headerdirectives forward important information like the user's IP address.
-
Restart Nginx: After configuring, you need to restart Nginx to apply the changes:
sudo systemctl restart nginx -
Test the Reverse Proxy: You can test the reverse proxy by accessing
http://example.comin a browser. If configured correctly, Nginx will forward the request to the backend server and return the results to the user.
Configuring Reverse Proxy with Apache
Apache is also a popular choice for setting up a reverse proxy. To configure a reverse proxy on Apache, follow these steps:
-
Install Apache: Install Apache on your system with the command:
sudo apt update sudo apt install apache2 -
Enable Proxy Modules: Apache needs the
mod_proxymodule to act as a reverse proxy. You need to enable this module with the following commands:sudo a2enmod proxy sudo a2enmod proxy_http sudo systemctl restart apache2 -
Configure Reverse Proxy: Open the Apache configuration file:
sudo nano /etc/apache2/sites-available/000-default.confAdd the reverse proxy configuration to the file:
<VirtualHost *:80> ServerAdmin webmaster@localhost ServerName example.com ProxyPass / http://localhost:8080/ ProxyPassReverse / http://localhost:8080/ ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined </VirtualHost>Here:
ProxyPassis the backend server address to which the reverse proxy will forward requests.ProxyPassReverseensures that the headers returned from the backend server are properly processed when sent back to the user.
-
Restart Apache: After configuring, restart Apache:
sudo systemctl restart apache2 -
Test the Reverse Proxy: Access
http://example.comin a browser to check if the reverse proxy is working correctly.
Notes When Using Reverse Proxy
- Security: When deploying a reverse proxy, make sure you have configured proper security, such as using SSL to encrypt connections and ensuring that only valid requests are forwarded to the backend server.
- Performance Monitoring: To ensure the reverse proxy does not become a bottleneck, monitor the traffic and performance of Nginx or Apache. Tools like nginx-status or Apache mod_status can help monitor system activity.
- Scalability: If your system has high traffic, consider configuring the reverse proxy to scale flexibly, such as using load balancing tools.
By properly configuring and using reverse proxy, you can enhance the security, performance, and management capabilities of your web system.
Conclusion
Reverse Proxy is a powerful technology that enhances security, improves performance, and optimizes traffic management for web systems. With features like load balancing, backend server protection, and support for SSL termination and caching, reverse proxy plays an important role in building modern web applications and services.
Although there are many benefits, deploying a reverse proxy requires careful consideration of factors such as scalability, security, and compatibility with applications. To achieve optimal results, you need to configure the reverse proxy correctly and monitor system performance regularly.
If you are looking to optimize your web system or protect backend servers from external threats, reverse proxy is a robust solution. Whether using Nginx, Apache, or other tools, implementing reverse proxy will help you create a more stable and secure system.
Make sure you fully understand your system's needs and configure reverse proxy accordingly to maximize the potential of this technology.
Latest Posts

Lesson 26. How to Use break, continue, and return in Java | Learn Java Basics
A guide on how to use break, continue, and return statements in Java to control loops and program execution flow effectively.

Lesson 25. The do-while Loop in Java | Learn Basic Java
A detailed guide on the do-while loop in Java, including syntax, usage, examples, and comparison with the while loop.

Lesson 24. How to Convert Decimal to Binary in Java | Learn Basic Java
A guide on how to convert numbers from the decimal system to the binary system in Java using different methods, with illustrative examples.

Lesson 23. How to Use the While Loop in Java | Learn Java Basics
Learn how to use the while loop in Java with syntax, real-world examples, and practical applications in Java programming.
Related Posts

What is .htaccess? Guide to Editing and Configuring .htaccess
Learn about the .htaccess file, its functions, and how to edit and configure .htaccess to optimize security, SEO, and website performance.

What is DNS? The Mechanism of Domain Name Resolution System
Learn about DNS, the mechanism of the domain name resolution system, and the important role of DNS in maintaining website operations.

What is a Dedicated Server? A Guide to Choosing the Right Dedicated Server
Learn about Dedicated Servers, the benefits of using a dedicated server, and how to choose the right one for your needs.
Difference Between Web Server and Application Server
Learn the difference between Web Server and Application Server – two essential servers in web technology systems. Explore their structure, functions, how they work, and when to use each type of server.

