Understanding What Proxy Is? – Concept, How It Works, and Applications
- Published on

- What is Proxy?
- Functions of Proxy Server
- Proxy Classification
- Forward Proxy
- Reverse Proxy
- Summary
- Mechanism of Proxy Server
- Real-World Applications of Proxy
- Privacy Protection and Anonymity
- Accessing Blocked or Geo-Restricted Content
- Managing and Monitoring Network Traffic in Businesses
- Enhancing Network Security
- Speeding up Web Access
- Improving Website Performance and Load Distribution
- Basic Proxy Usage Guide
- Finding Free Proxy Sources
- Implementing Proxy with Python
- How to Set Up a Proxy for Google Chrome
- Setting Up Proxy Through System Settings (Windows/Mac)
- Using an Extension to Set Up Proxy
- Where to Buy Reliable Proxies
- Paid and Bonafide Proxies
- Proxies for Businesses
- Choosing the Right Proxy for Your Needs
- Frequently Asked Questions About Proxies
- What is Rotating Proxy?
- Why is it sometimes slower when I use a proxy?
- Can proxies be used for all types of websites?
- The Difference Between IPv4 and IPv6 Proxies
- Conclusion
What is Proxy?
Proxy (or proxy server) is an intermediary server that acts as a middleman between the user and the Internet. When you make a request to a website, the request does not go directly to the website; instead, it is sent to a proxy server. The proxy server then accesses the website on your behalf, retrieves the data, and forwards it back to you. This can help mask the user's identity, increase browsing speed, or even bypass geographic restrictions when accessing online services.
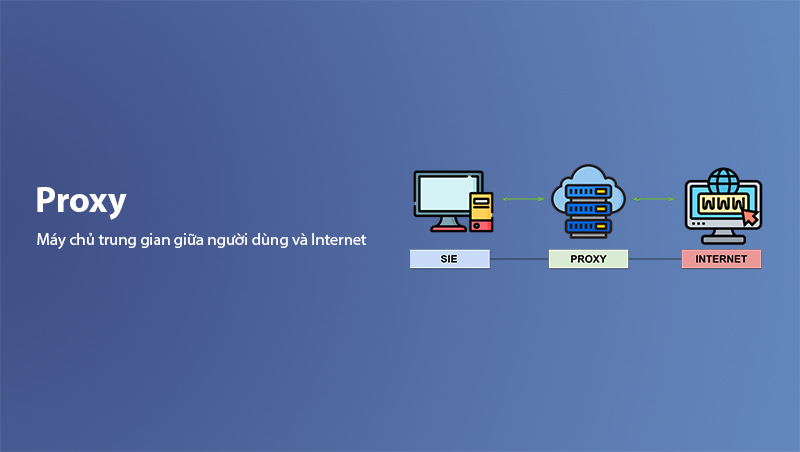
A proxy server can serve many purposes, from securing internal networks to optimizing internet speeds by temporarily storing data from user requests. Thanks to proxies, users can access websites more quickly and securely, as well as manage and control traffic in business environments.
A common example of proxy is when you use a VPN (Virtual Private Network) to change your IP address when accessing online services. In this case, the VPN acts as a type of proxy to hide your real IP address and protect your privacy when using the internet.
Functions of Proxy Server
A proxy server performs many important functions in a network system, improving performance, security, and access control. Here are the main functions of a proxy server:
-
Privacy and Security: When using a proxy server, the user's real IP address is hidden. The proxy sends the request and receives the response on behalf of the user. This helps protect the user's privacy and reduces the risk of external attacks. Proxy servers can also help prevent DDoS attacks and protect internal networks from online threats.
-
Bandwidth Saving and Performance Optimization: A proxy can cache (temporarily store) data from websites that users frequently visit. When the next request is made by the same or another user, the proxy can return the cached data instead of retrieving it from the internet, saving bandwidth and reducing page load times.
-
Content Control and Filtering: Proxy servers allow organizations and businesses to manage and control users' internet traffic. They can use proxies to filter unwanted or unsafe websites, blocking access to websites containing harmful or inappropriate content in the workplace.
-
Bypassing Geographical Restrictions: Proxies can help users bypass geographic restrictions when accessing online services. By connecting to a proxy server in another country, users can simulate being in that location and access region-restricted content.
Thanks to these functions, proxy servers are powerful tools for protecting personal information, improving internet performance, and helping users control and optimize network traffic.
Proxy Classification
Proxies can be divided into two main groups: Forward Proxy and Reverse Proxy. Here are the detailed classifications of each group:
Forward Proxy
Forward Proxy is a type of proxy that sits between the user and the internet. When a user sends a request to a server on the internet, the request is sent to the proxy and then forwarded to the target server.
Some types of proxies under the Forward Proxy group:
-
Anonymous Proxy: A proxy that helps hide the user's real IP address while browsing the web. This proxy protects the user's privacy by not disclosing their actual IP address, but the target server can still identify that the request is coming from a proxy.
-
High Anonymity Proxy (Elite Proxy): A type of Anonymous Proxy, but with higher security. In addition to hiding the real IP address, this proxy also conceals its existence, making it impossible for the target server to recognize that the request is being handled by a proxy. This is the type of proxy that offers the highest level of anonymity and security.
-
Transparent Proxy: This type of proxy is undetectable by the user during web browsing. While the proxy still processes requests, the user does not need to configure anything special. Transparent Proxy is mainly used in organizations to filter content and control access.
-
Caching Proxy: A proxy configured to temporarily store web content that the user has accessed before. When the next request comes, the proxy can return the cached data, saving bandwidth and speeding up browsing.
-
Open Proxy: A public proxy, allowing anyone to use it without authentication. However, because it is public, open proxies can be security risks and are often exploited for malicious purposes.
Reverse Proxy
Reverse Proxy works the opposite of Forward Proxy. It sits between the user and one or more backend servers, receiving requests from users and forwarding them to the appropriate server. Responses from the backend server are also forwarded back to the users via the reverse proxy.
Main functions of Reverse Proxy:
- Load Balancing: Helps distribute traffic to multiple backend servers, reducing the load on individual servers.
- Security: Reverse proxy can help protect backend servers from direct attacks from the internet.
- Performance Improvement: Reverse proxy can use techniques like caching to reduce the load on servers and increase access speed.
- SSL Termination: Reverse proxy can handle encryption and decryption of SSL data, allowing backend servers to only process unencrypted requests, reducing the load on servers.
Summary
- Forward Proxy: A proxy between the user and the internet, including types like Anonymous Proxy, Transparent Proxy, Caching Proxy, and Open Proxy.
- Reverse Proxy: A proxy between the user and backend servers, mainly used for load balancing, security, and performance improvement.
With this clear classification, you will easily understand the purposes and choose the right type of proxy for specific scenarios.
Mechanism of Proxy Server
A proxy server acts as an intermediary between the user and the internet. When a user wants to access a website, instead of sending the request directly to the website’s server, the request is sent to the proxy server. The proxy server processes this request, sends it to the destination server, and returns the result to the user.
Here is a detailed description of the mechanism of proxy:
-
User Sends Request: The user enters the web address into the browser. Instead of sending the request directly to the target website's server, the browser sends the request to the proxy server.
-
Processing the Request at Proxy: The proxy server receives the request from the user and checks conditions like security, cache, or content filtering. If the website has been cached by the proxy, it will return that data without needing to fetch it from the internet.
-
Sending Request to Target Server: If the proxy doesn't have cached data or the request needs to be sent out, it will forward the request to the destination website's server.
-
Returning Result to User: After the destination server returns data (e.g., webpage, image, video), the proxy sends this data back to the user, making the user unaware of the real IP address of the original server or the external network.
-
Security and Control: During this process, the proxy can apply security measures like encryption, content filtering, or access control to ensure that the requests and responses are handled securely and correctly.
This mechanism helps improve access speed, protect users' privacy, and minimize security risks for internal networks. By using a proxy, organizations can easily control and monitor internet traffic, protecting systems and sensitive data from external threats.
Real-World Applications of Proxy
Proxy servers not only play a significant role in improving performance and security but are also used in many real-world applications across various fields. Here are some common applications of proxy:
Privacy Protection and Anonymity
One of the most common uses of proxy is for privacy protection while browsing the web. Forward Proxies like Anonymous Proxy or Elite Proxy help users hide their real IP addresses and protect personal information from being tracked by websites and online services. This is particularly useful for users who want to browse the web anonymously or avoid being tracked by advertising tools.
Accessing Blocked or Geo-Restricted Content
Proxy can help users bypass geographic restrictions or bypass firewalls, allowing access to blocked or restricted websites in certain countries. For example, many services like Netflix or YouTube may restrict content to be viewed only in certain countries. By using a proxy, users can "fake" an IP address from another country and access that content.
Managing and Monitoring Network Traffic in Businesses
In internal networks of businesses, proxy is often used to control and monitor network traffic. Organizations can use proxy to filter content (block inappropriate websites), save bandwidth (by caching popular content), and monitor employees' internet access activities. This helps protect the network system and improve work efficiency.
Enhancing Network Security
Reverse Proxy plays a critical role in enhancing security for network systems. When using reverse proxy, backend servers do not directly handle requests from the outside. Instead, the reverse proxy processes all requests, helping to prevent DDoS attacks and protect servers from direct attacks from the internet. Furthermore, reverse proxy can also perform tasks like SSL encryption, reducing the load on the backend web servers.
Speeding up Web Access
Another application of proxy is speeding up web browsing. Proxy servers can cache previously accessed content in cache memory. When users request the same content again, the proxy can immediately return the data without needing to reload it from the original server, helping to minimize wait times and save bandwidth.
Improving Website Performance and Load Distribution
Reverse Proxy can help improve the performance of websites with high traffic. Reverse Proxy helps distribute the load to multiple backend servers, ensuring that user requests are processed evenly without degrading server performance. This helps ensure that the website remains stable even with high concurrent access.
Thus, the practical applications of proxy extend beyond just improving performance and security, covering areas like privacy protection, bypassing geographic restrictions, or more effective network management in organizations.
Basic Proxy Usage Guide
Using a proxy in applications, browsers, or web services can help increase security, improve performance, or bypass geographic restrictions. Here are some basic steps for using a proxy:
Finding Free Proxy Sources
If you are just starting and don’t want to spend on paid proxy services, you can begin with free proxies. However, be aware that free proxies are often insecure, unstable, and may have speed limitations. Here are some ways to find free proxies:
- Search on websites offering free proxies: Websites like Free Proxy List, ProxyScrape, or Hide My Ass provide free proxy lists with IP addresses and ports for you to use.
- Use automated proxy discovery tools: Some tools automatically scan and provide free proxies, saving you time searching.
Note: Free proxies are not guaranteed to be secure and may be exploited. If you need better security and stability, consider using paid proxies.
Implementing Proxy with Python
If you're a developer and want to use proxies in your applications, you can implement proxies using Python. Python has many libraries that support proxy usage, such as requests, http.client, or PySocks.
Example of using the requests library to set up a proxy:
import requests
# Configure proxy
proxies = {
'http': 'http://username:password@proxy_address:port',
'https': 'https://username:password@proxy_address:port',
}
# Send request with proxy
response = requests.get('http://example.com', proxies=proxies)
print(response.text)
In the example above, you need to replace proxy_address, port, username, and password with actual information from the proxy you use. You can also select proxies for HTTP and HTTPS protocols separately.
Through Python and related libraries, you can implement proxies flexibly in your applications, optimizing web browsing tasks, information checks, or security when using the internet.
Using proxy is quite simple, and you can apply it for various purposes such as privacy protection, bypassing geographic restrictions, or improving network performance. However, make sure to choose reliable proxies, especially when using services related to security or critical operations.
Sure, here’s the full translation of your content into English, keeping the original image URLs and HTML structure intact:
How to Set Up a Proxy for Google Chrome
If you want to use a proxy in the Chrome browser to improve performance, security, or bypass geographic restrictions, you can easily configure the proxy directly from the browser settings or through the system. Below is a detailed guide to setting up a proxy for the Google Chrome browser.
Setting Up Proxy Through System Settings (Windows/Mac)
Google Chrome uses the system’s proxy settings to connect to the internet, so you will need to change the proxy settings in your operating system.
Setting up proxy on Windows:
- Open Control Panel and select Network and Internet.
- Select Internet Options.
- In the Internet Properties window, select the Connections tab, then click on LAN settings.
- Check Use a proxy server for your LAN.
- Enter the proxy address and port in the appropriate fields.
- Click OK to save the settings.
Setting up proxy on Mac:
- Open System Preferences and select Network.
- Choose the connection you are using (Wi-Fi or Ethernet), then click Advanced.
- Select the Proxies tab.
- Choose the proxy protocol you want to use (HTTP, HTTPS, SOCKS, etc.), then enter the proxy address and port.
- Click OK and Apply to save the settings.
Once configured, Chrome will automatically use these proxy settings to access the internet.
Using an Extension to Set Up Proxy
If you do not want to change the system-wide proxy settings, you can use proxy extensions for Chrome, allowing you to configure a proxy only for the browser without changing the system settings.
Some popular proxy extensions for Chrome:
- Proxy SwitchyOmega: Allows you to easily switch between different proxy configurations.
- FoxyProxy: A powerful tool that helps you manage and switch between multiple proxies.
To install a proxy extension:
- Visit the Chrome Web Store and search for proxy extensions like Proxy SwitchyOmega or FoxyProxy.
- Click Add to Chrome to install the extension.
- After installation, open the extension and enter the proxy address and port.
- Select the proxy you want to use, then Chrome's requests will be routed through that proxy.
Using a proxy extension allows you to easily switch between proxies without altering the entire system configuration.
With these steps, you can easily set up and use a proxy in the Chrome browser to protect privacy, speed up web browsing, or bypass geographical restrictions. Using a proxy not only helps you browse the web more securely but also optimizes your online experience.
Where to Buy Reliable Proxies
When you need to use a proxy for important purposes such as security, bypassing geographical restrictions, or managing network traffic in an organization, choosing a reliable proxy provider is crucial. Trusted proxy providers not only ensure the quality of service but also protect your personal information and maintain stable performance.
Here are some reliable places to buy proxies that you can refer to:
Paid and Bonafide Proxies
Paid proxy providers typically offer higher stability and better security compared to free proxies. Below are some popular and trusted proxy services:
-
Luminati (Bright Data): One of the most reputable proxy services, offering various types of proxies such as Residential Proxy, Mobile Proxy, and Datacenter Proxy. Luminati has a vast network with millions of IPs worldwide, allowing you to maintain anonymity and bypass geographical restrictions easily.
-
Smartproxy: Provides residential proxy and datacenter proxy with high speeds and robust security. This service is ideal for companies looking to collect data or bypass IP restrictions.
-
Oxylabs: Offers high-quality proxy services with residential proxies, datacenter proxies, and mobile proxies. Oxylabs is known for its stable performance and excellent customer support.
-
ScraperAPI: If you are looking for a proxy for data scraping without encountering restrictions, ScraperAPI offers perfect proxy services for scraping tasks with millions of IPs available and automatic CAPTCHA solving support.
Proxies for Businesses
For businesses or organizations, dedicated business proxy services can offer advanced features such as load balancing, SSL termination, and network performance optimization. These services not only help protect and optimize internet connections but also support traffic analysis and monitoring. Some prominent business proxy services include:
-
Amazon Web Services (AWS) – Amazon CloudFront: Offers reverse proxy services to optimize websites and deliver content quickly.
-
Cloudflare: Provides a powerful reverse proxy, protecting websites from DDoS attacks and optimizing website speed.
-
ProxyMesh: A proxy service for businesses that provides proxies from IPs in different geographic areas, improving the ability to maintain anonymity and bypass geographical bans.
Choosing the Right Proxy for Your Needs
When selecting where to buy proxies, consider the following factors:
- Purpose: Determine your purpose (security, bypassing geographical restrictions, data collection, etc.).
- Security: Choose proxy services that offer high security to avoid exposing personal information.
- Cost: Paid proxies generally offer more features and better service, but you also need to consider your budget.
With trusted proxy providers like Luminati, Smartproxy, or Oxylabs, you can obtain high-quality, secure, and stable proxy solutions for personal or business needs. Make sure to choose a proxy that aligns with your purpose and budget for optimal results.
Frequently Asked Questions About Proxies
When using a proxy, users often encounter some common questions and issues. Below are some frequently asked questions about proxies along with detailed answers:
What is Rotating Proxy?
A rotating proxy is a type of proxy that changes the IP address continuously every time the user sends a request. This helps to maintain anonymity and avoid being blocked when sending many requests from a single IP address. Rotating proxies are commonly used for data scraping and bypassing IP restrictions on websites.
Why is it sometimes slower when I use a proxy?
When using a proxy, internet speed may be slower than usual for several reasons:
- Free or low-quality proxies: Unreliable proxies often have slower and unstable speeds due to being overloaded or poorly optimized.
- Geography and distance: If the proxy is located far from the server or user, the response time will be longer, causing reduced speed.
- Too many users: Public or shared proxies may be overloaded due to many users sharing the same IP address.
- Security and encryption: Proxies using high security or encryption (such as VPN proxies) can slow down the speed due to the encryption and decryption process.
To improve speed, you should use reliable and high-quality proxies.
Can proxies be used for all types of websites?
Proxies can be used for most websites, but there are some cases where proxies may be blocked by websites or services, especially when websites use tools to detect and prevent proxy usage. Some streaming services like Netflix, Hulu, or YouTube may detect proxies and block users if they find out they are using a proxy.
The Difference Between IPv4 and IPv6 Proxies
When it comes to proxies, you will encounter two common types of IP addresses: IPv4 and IPv6. Each type has its own distinct features and applications, especially when you are using proxies for anonymity, bypassing geographical restrictions, or network management.
IPv4 Proxy
IPv4 is the most commonly used IP address version and has been around for a long time. IPv4 addresses consist of four groups of numbers (e.g., 192.168.1.1), each ranging from 0 to 255, creating an address space of about 4 billion usable addresses. However, due to the rapid growth of the internet and connected devices, the number of available IPv4 addresses has become limited.
IPv4 proxies are typically used for purposes such as:
- Maintaining online anonymity: IPv4 proxies can help change the user's IP address to avoid tracking or blocking access to websites.
- Bypassing geographical restrictions: IPv4 proxies can allow users to access content that is blocked in their region by simulating an IP address from another country.
However, when using IPv4 proxies, users may encounter some issues, especially when multiple users share a single proxy address. This can lead to decreased network performance and make it easier for websites to detect and block the proxy.
IPv6 Proxy
With the rapid development of the Internet of Things (IoT) and the increasing number of connected devices, IPv6 was introduced to address the shortage of addresses in IPv4. IPv6 provides a much larger address space, with nearly 340 undecillion (3.4 x 10^38) addresses, solving the growing need for connectivity.
IPv6 proxies offer some significant benefits:
- Unique IP addresses: IPv6 proxies provide a unique and abundant IP address, minimizing the risk of being detected and blocked by web services.
- Higher security potential: With a larger address space, IPv6 proxies are harder to attack or scan, providing better protection for users.
However, since IPv6 is still not as widely adopted as IPv4, using IPv6 proxies may encounter some compatibility issues with older systems or services that do not support IPv6.
The Difference Between Residential and Data Center Proxies
An important distinction when it comes to proxies is between residential proxies and data center proxies.
- Residential Proxy: Provided by Internet service providers to households, residential proxies offer real IP addresses and can be used to simulate the user's real location. Since these are real user IPs, residential proxies are harder to detect and block, making them great for bypassing website security mechanisms.
- Data Center Proxy: Provided by data centers and typically virtual IPs, data center proxies are easier to detect and block. However, they tend to be faster and cheaper than residential proxies, making them suitable for tasks that do not require high anonymity.
Thus, the choice between IPv4 proxy and IPv6 proxy depends on your needs, with IPv6 offering higher security and residential proxies providing better anonymity. Combining these proxies in the right way will help you achieve optimal results in practical applications.
Conclusion
In today's connected world, proxies have become an incredibly useful tool for both individual users and businesses. Whether you are looking for a solution to protect privacy, bypass geo-restrictions, or optimize browsing speed and bandwidth, proxies can meet most of these needs. However, selecting the right type of proxy and a trusted provider is crucial to ensuring effectiveness and security.
Through types of forward proxies, reverse proxies, and caching proxies, you can improve your web experience, protect personal data, and even save costs for businesses. Using paid proxies from trusted providers like Luminati, Smartproxy, or Oxylabs will help you avoid security and speed issues typically encountered with free proxies.
Proxies are not only useful for individuals but also play a critical role in the security and optimization strategies of businesses. To achieve the best results, you should choose a proxy service that suits your needs and ensures security, performance, and stability.
We hope this article has helped you understand more about proxies, how to use them, and their applications. If you have any questions or need more information, feel free to leave a comment or contact us!
With this knowledge, you can confidently use proxies for your personal or business needs, ensuring online safety and optimizing web experiences effectively.
Latest Posts

Lesson 26. How to Use break, continue, and return in Java | Learn Java Basics
A guide on how to use break, continue, and return statements in Java to control loops and program execution flow effectively.

Lesson 25. The do-while Loop in Java | Learn Basic Java
A detailed guide on the do-while loop in Java, including syntax, usage, examples, and comparison with the while loop.

Lesson 24. How to Convert Decimal to Binary in Java | Learn Basic Java
A guide on how to convert numbers from the decimal system to the binary system in Java using different methods, with illustrative examples.

Lesson 23. How to Use the While Loop in Java | Learn Java Basics
Learn how to use the while loop in Java with syntax, real-world examples, and practical applications in Java programming.
Related Posts

What is .htaccess? Guide to Editing and Configuring .htaccess
Learn about the .htaccess file, its functions, and how to edit and configure .htaccess to optimize security, SEO, and website performance.

What is DNS? The Mechanism of Domain Name Resolution System
Learn about DNS, the mechanism of the domain name resolution system, and the important role of DNS in maintaining website operations.

What is a Dedicated Server? A Guide to Choosing the Right Dedicated Server
Learn about Dedicated Servers, the benefits of using a dedicated server, and how to choose the right one for your needs.
Difference Between Web Server and Application Server
Learn the difference between Web Server and Application Server – two essential servers in web technology systems. Explore their structure, functions, how they work, and when to use each type of server.

